Nomad Hack - the first decentralized robbery and what it meant for you
The cross-chain token bridge Nomad was exploited on Monday. The protocol loses nearly $200 million in the so-called most chaotic hacks that Web3 has ever seen. Let's dig into this article and uncover one of the most brutal yet interesting hacks ever.

Chainalysis, a blockchain data platform, estimates that $2 billion in cryptocurrency has been stolen from cross-chain bridges across 13 separate hacks this year (so far). 2 billion dollars includes the latest exploit of the Nomad Bridge.
This raises the issue of trust in blockchain technology. As more value flows through cross-chain bridges, they become more attractive victims for hackers.
TL;DR
- Cross-chain bridge Nomad got hacked for nearly $200 million on Monday, August 01, 2022.
- This was later named the first decentralized robbery or free-for-all exploitation since everyone can be able to grab money from the protocol.
- Nomad has yet to confirm the cause, but experts explain that a recent update to one of Nomad's smart contracts made it easy for users to spoof transactions. More specifically, a smart contract flaw accepts all the transactions without checking the issuer's balance.
- Unlike previous bridges attacks on Ronin, Wormhole,..., where hackers need to control the private key, the attacks on Nomad are quite simpler. All you had to do was find a transaction that worked, find/replace the other hacker's address with yours, and then re-broadcast it.
- Seem like there is no practical way to recover the money other than the hackers returning the money themself.
- Nomad is currently working on the Investigation/Recovery process, which is mostly by calling help from whitehat hackers and tracing all the funds. Today, August 04, they tweeted that they have recovered a total of $16.6m.
- Cross-chain is one way to communicate between chains, but it is ineffective. Due to the large value of assets they often hold and the complexity (and thus potential vulnerability) of the smart contract code they run on, they become a vulnerable target. $2 billion in cryptocurrency has been stolen from cross-chain bridges across 13 separate hacks this year (so far).
- "the future will be *multi-chain*, but it will not be *cross-chain*" - said Vitalik Buterin.
- Take out from this incident: Do not put all your money on the bridge. If you want to put some money in, check its security carefully.
Introducing The First Decentralized Robbery
If you are not familiar with Nomad, it is a cryptocurrency bridge that allows users to send and receive tokens between blockchains like Avalanche (AVAX), Ethereum (ETH), Evmos (EVMOS), Moonbeam (GLMR), Milkomeda C1.
Also, here is their introduction:
"Nomad is an optimistic interoperability protocol that enables secure cross-chain communication.
Using Nomad:
- Users can bridge tokens between chains
- Asset issuers can deploy tokens across chains
- DAOs can facilitate the execution of cross-chain governance proposals
- Developers can build native cross-chain applications (xApps)
The goal of Nomad is to provide the connective tissue to enable users and developers to interact securely in a multi-chain world."
“We’re secure… period” — @pranaymohan
— Nomad (⤭⛓🏛) (@nomadxyz_) January 27, 2022
And they have become the victim of crypto's latest nine-figure attack, aka the Nomad Hack.
The first sign of trouble began at about 9:23 pm UTC after a hacker exploited the bridge to withdraw 100 WBTCs worth $2.3 million.
Several others copied the code of the first suspicious transaction and changed the address to participate in draining the funds.
Bizarrely, some of the exploit transactions had the same value. For instance, there were over 200 transactions of exactly 202,440.725413 USDC.
We are aware of the incident involving the Nomad token bridge. We are currently investigating and will provide updates when we have them.
— Nomad (⤭⛓🏛) (@nomadxyz_) August 1, 2022
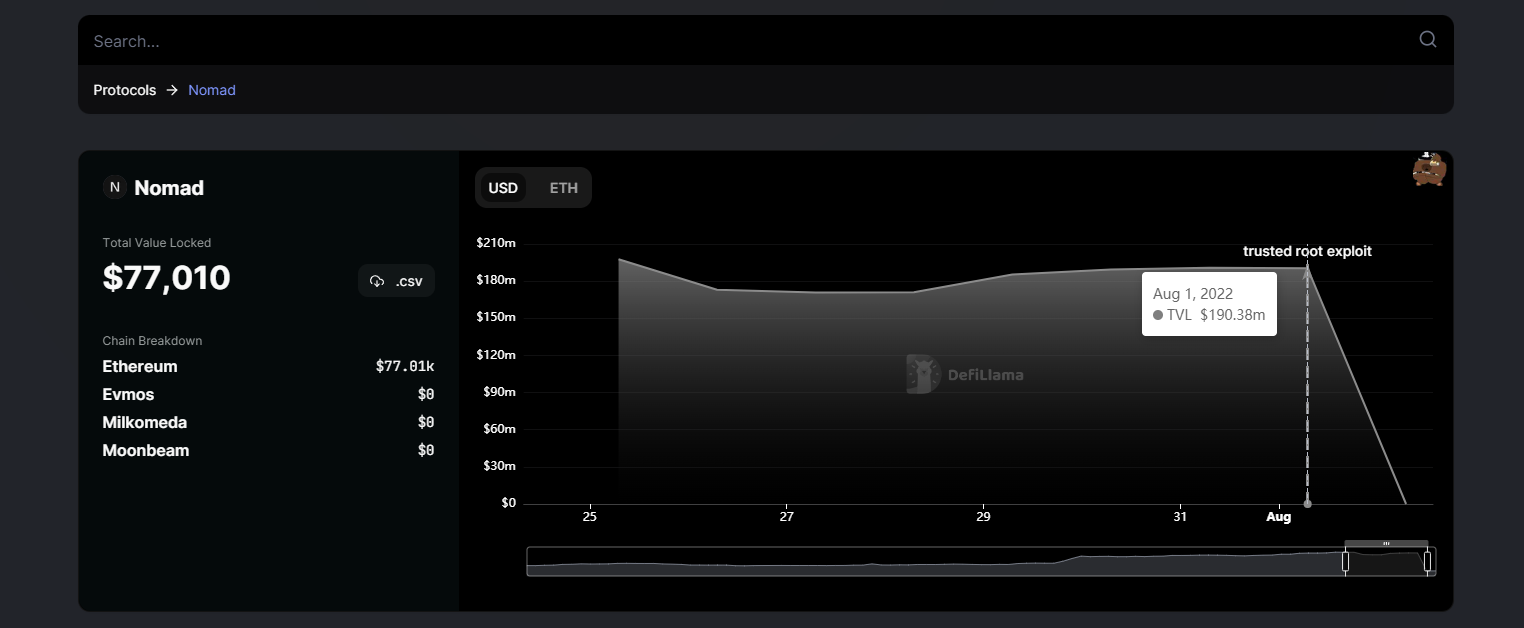
Nomad told users Monday evening via a tweet that it was "aware of the incident involving the Nomad token bridge." By then, the protocol had lost $45 million.
According to the Dune analyst by @1kbeetlejuice, in the next 2 hours, Nomad's smart contract was drained, decreasing from 176.6 million USD to almost zero.
The protocol told users it was "aware of impersonators posing as Nomad and providing fraudulent addresses to collect funds." By midnight on Monday, the protocol had lost nearly $200 million.
Nomad stated today:
8-1-2022 incident update pic.twitter.com/EX8r4Ybvre
— Nomad (⤭⛓🏛) (@nomadxyz_) August 2, 2022
The attack comes two months after the bridge received extensive funding from Coinbase Ventures, OpenSea, and many major crypto companies. This funding round pushed Nomad's valuation to $225 million.
Unlike other crypto exploits where only a few addresses are directly tied to the hack, hundreds of addresses were responsible for draining the Nomad bridge of almost all the $190.7 million locked in it.
Blockchain security experts described the exploit as a "free-for-all." Anyone with knowledge of the exploit and how it worked could seize on the flaw and withdraw a number of tokens from Nomad — sort of like a cash machine spewing out money at the tap of a button.
According to PeckShield, 41 addresses grabbed over $152 million in the Nomad bridge exploit.
FatMan from the Terra Research Forum tweeted: "In true crypto fashion - the first decentralized robbery."
Messages popping up in public Discord servers of random people grabbing $3K-$20K from the Nomad bridge - all one had to do was copy the first hacker's transaction and change the address, then hit send through Etherscan. In true crypto fashion - the first decentralized robbery. https://t.co/jWV9AamBer
— FatMan (@FatManTerra) August 2, 2022
Visually, the "attack" looks like this:
After this major attack, Nomad landed on the list of biggest exploits in 2022. However, this hack was slightly different from the others as the funds drained out the protocol over hours and in small batches.
What really happen?
Nomad has yet to confirm how hackers were able to steal the funds.
Sam Sun (samczsun), a research partner at crypto-focused investment firm Paradigm, explained that a recent update to one of Nomad's smart contracts made it easy for users to spoof transactions. This meant users were able to withdraw money from the Nomad bridge that didn't actually belong to them.
1/ Nomad just got drained for over $150M in one of the most chaotic hacks that Web3 has ever seen. How exactly did this happen, and what was the root cause? Allow me to take you behind the scenes 👇 pic.twitter.com/Y7Q3fZ7ezm
— samczsun (@samczsun) August 1, 2022
"... [Y]ou didn't need to know about Solidity or Merkle Trees or anything like that. All you had to do was find a transaction that worked, find/replace the other person's address with yours, and then re-broadcast it," @samczsun explained.
It started with an upgrade to Nomad's code. One part of the code was marked as valid whenever users decided to initiate a transfer, which allowed thieves to withdraw more assets than were deposited into the platform. Once other attackers cottoned on to what was going on, they deployed armies of bots to carry out copycat attacks.
10/ It turns out that during a routine upgrade, the Nomad team initialized the trusted root to be 0x00. To be clear, using zero values as initialization values is a common practice. Unfortunately, in this case it had a tiny side effect of auto-proving every message pic.twitter.com/fA3XbNW9qT
— samczsun (@samczsun) August 2, 2022
Basically, this meant that when a user transferred funds from one blockchain to another, Nomad turned the light green, enabling the user to withdraw funds that didn't belong to them.
It's like a central bank that accepts all the issued transactions without checking the users' balance.
In Nomad's case, a user could send 1 ETH, then manually call the smart contract on the other blockchain to receive 100 ETH. And the crazy thing is, the protocol accepts it.
Someone (the attacker) seized this opportunity and exploited the smart contract itself.
"a routine upgrade marked the zero hash as a valid root, which had the effect of allowing messages to be spoofed on Nomad. Attackers abused this to copy/paste transactions and quickly drained the bridge in a frenzied free-for-all" - said @samczsun.

The Domino effect happened. That is why up to 41 addresses grabbed over $152 million in the exploit, and many exploit transactions had the exact value of 202,440.725413 USDC.
Like a few previous attacks, Nomad was targeted through a flaw in its code. But there were a few differences. With previous attacks, hackers were able to retrieve the private keys needed to gain control over the network and start moving out tokens. In Nomad's case, it was much simpler than that. A routine update to the bridge enabled users to forge transactions and make off millions' worth of cryptocurrency.
History of Cross-chain Bridge Attacks
Cross-chain bridges are designed to solve the challenge of interoperability between different blockchains. A cross-chain bridge is a protocol that lets a user port assets from one blockchain to another.
I made a chart of the largest bridge exploits this year.
— Edgy - The DeFi Edge 🗡️ (@thedefiedge) August 3, 2022
It's surreal how big the Ronin Network (Axie's Infinity) exploit is. pic.twitter.com/qVi7sWT7G2
While bridge designs vary, users typically interact with cross-chain bridges by sending funds in one asset to the bridge protocol, where those funds are then locked into the contract. The user is then issued equivalent funds of a parallel asset on the chain the protocol bridges to.
Bridges are an attractive target because they often feature a central storage point of funds that back the "bridged" assets on the receiving blockchain.
Ronin Bridge Exploit

The Ronin Bridge Exploit is the largest DeFi exploit ever committed. At the end of March, Ronin, an ETH sidechain built for Axie Infinity, was hacked for over 173,600 ETH and 25.5 million USDC, worth over $600 million. The company officially reported that the hackers compromised five validator nodes to get access to private keys. The Ronin chain consisted of nine validator nodes, and the hackers managed to get access to four of them along with a third-party validator run by decentralized autonomous organization Axie DAO.
Wormhole Bridge Exploit

On February 02, 2022, the second largest cross-chain bridge exploit occurred on the Wormhole Bridge. In this incident, the attacker bypassed the protocol's verification process, leading to 120,000 Wormhole Ethereum (WeETH) lost. During the attack, the hacker bypassed the verification step by injecting a fake sysvar account and successfully generated a malicious "message" that specified 120,000 wETH to be minted. By invoking the "complete_wrapped" function with the malicious "message", the attacker successfully minted 120,000 wETH. Two minutes after the minting, the exploiter bridged 10,000 ETH to the Ethereum blockchain and another 80,000 ETH transaction occurred on the Ethereum blockchain about 20 minutes later. To this day, the funds are still sitting in the attacker's wallets.
Harmony Exploit

On June 23, 2022, the bridge between Harmony chain and Ethereum experienced multiple exploits. That includes ETH, USDC, WBTC, USDT, DAI, BUSD, AAG, FXS, SUSHI, AAVE, WETH, and FRAX. The transactions vary in value but range from $49,178 to upwards of $41,200,000. The attacker accomplished this by controlling the owner of the MultiSigWallet to call the confirmTransaction() directly to transfer large amounts of tokens from the bridge on Harmony, which led to a total loss of around $97M worth of assets on the Harmony chain.
Qubit Exploit

On January 27, 2022, Qubit was hacked for $80 million. In this exploit, the attacker called in the QBridge contract without any ETH attached to this transaction. The hacker abused the functions of the QBridge contract and faked an ETH event with an ERC20 event. Faking the ETH event enabled the malicious actor to pass the validation in the QBridgeHandler and mint around 77,162 qxETH in the crossed chain. The hacker then deposited the stolen funds into Tornado Cash.
And now, we have the Nomad Exploit, with nearly $200 million hacked.
What it meant for you
Since this is a decentralized robbery, it's not much you can do about it.
Nomad is working on the Investigation/Recovery process. That involves many leading chain analysis/intelligence firms and law enforcement to trace and recover funds.
Maybe some of the funds will be recovered from the tracing, lawsuit, etc. But that will probably take years and years in the courtroom.

In a more optimistic take, crypto experts suggested that the funds could be reclaimed from the whitehats that drained preventively. Nomad is also calling whitehats to recover funds. And yes, Hackers have sent back $9 million to Nomad a day after the cross-chain bridge was exploited.
If you have money on the bridge during the attack, well, good luck.
If you tend to put money on Nomad or other cross-chain bridges, please read the following texts.
As cryptocurrency investment grows, so does the incentive for criminal actors to exploit the crypto space.
Blockchain bridges are now routinely the targets of the most high-profile hacks in the cryptocurrency industry due to the large value of assets they often hold and the complexity (and thus potential vulnerability) of the smart contract code they run on.
Vitalik Buterin, co-founder of Ethereum, believes cross-chain bridges are inherently prone to security breaches.
"The fundamental security limits of bridges are actually a key reason why…I am pessimistic about cross-chain applications," Buterin wrote in a lengthy January Reddit post. The influential founder went on to express his belief that assets should be held in the same blockchain ecosystem, rather than shuffled between chains.
My argument for why the future will be *multi-chain*, but it will not be *cross-chain*: there are fundamental limits to the security of bridges that hop across multiple "zones of sovereignty". From https://t.co/3g1GUvuA3A: pic.twitter.com/tEYz8vb59b
— vitalik.eth (@VitalikButerin) January 7, 2022
"the future will be *multi-chain*, but it will not be *cross-chain*" - said Vitalik Buterin.
Here is the Vitalik's Reddit post, do check it our yourself:
Back to business, what do all of these attacks mean for you?
For developers, put up your defense, and do security audits regularly.
For users, be aware of the bridges or the bridges that you're investing in.
Some key lessons learned from these attacks:
- Separate the operation for depositing ETH with ERC20 by handling these cases differently.
- Always remember to verify the user-injected inputs.
- Keep an eye on recent exploits and check if the vulnerability exists in other projects that you are interested in.
- Core contracts from each bridge need to be audited.
And if bridge exploitation occurs:
- Stop relaying messages to pause any further token transfers across the network. For bridge contracts, pause the function to deposit and withdraw tokens.
- Inform communities, exchanges, and platform partners to monitor the flow of funds.
- Set up one communication channel and invite respected security experts to have effective discussions and information sharing.
- Identify, verify, and fix the vulnerability. Test to ensure the existing vulnerability is resolved and that no new vulnerability is introduced. Upgrade bridge contracts.
- Assess the damage and communicate transparently with your community about the amount exploited, assets that are recoverable/recovered, and any compensation programs to be set up.
Last but not least: Don't Put All your Eggs in One Basket. Peace.
